Latest News
Latest blogs and updates from SonicWall-Sales.com
The latest Sonicwall Secure Mobile Access and why you should upgrade
Remote working and flexible working are now a big part of the way we work, and businesses and their teams operate.
However, with this comes its own set of challenges.
For example, ensuring that everyone has fast and secure access to networks at any time from anywhere has become part of the norm. But it can also be challenging to provide, manage, and stay on top of.

For several years the Sonicwall Secure Remote Access solution was used for remote personnel located around the world. However, as times change, technology certainly moves at a pace with it.
In business today, we have more users, more applications, and more services than ever before. Ensuring that everyone’s needs and all system needs are taking care of, requires a high performing solution, with the remote access that is 100% secure.
Meet the latest in Sonicwall firewall security.
SMA, also known as Secure Mobile Access by Sonicwall, SMA offers a secure access gateway that is unified and enables businesses to provide access to applications and networks at any time from anywhere.
Offering clients more throughput, more memory, and more users.
It also has the features and capabilities to help businesses move to the cloud without hesitation or complication and welcome with open arms increased mobility and BYOD.
Reasons why people are upgrading to Sonicwall SMA
Smaller cost compared to a physical appliance
Going virtual can help to improve overall performance, offer increased flexibility and scalability, minimise upfront investment, reduce downtime, lower maintenance costs, and more!
Can operate faster
Having faster and more processing cores allows SMA to encrypt data in motion, with the results providing a higher and quicker performance experience for the user.
You can increase your throughput
We all want to deliver that seamless user experience, and by increasing your throughput, you can promote better productivity by providing faster access to network applications.
Serve more remote users
The SMA series offers much more scalability from a single appliance allowing you to manage a more significant number of users accessing the network remotely at the same time without it affecting speed or performance. (This can also be tracked with the firewalls.)
Supports increased bandwidth and data transfers
Organisations must be able to provide users with the necessary support to enable them to access bandwidth-intensive applications as well as carry out high-speed data transfers. With more high-speed ports on offer, the SMA provides the perfect solution.
Everything stays current
Patches must be kept current if they are to remain protected against up and coming as well as already established cyberthreats. All SMA firmware is packed with new features as well as advanced features for those requiring more.
Warranties are important
All IT functions need to ensure that the solution that is deployed is always fully supported, and it has a first-class warranty behind it.
Reduce administrative overheads
By centralising your management and reporting through automating routine tasks, businesses can make significant administrative savings. Freeing up valuable and much sought after time! With the Sonicwall Central Management Server (CMS), you will be provided with a single user administrative interface for all of your SMA appliance management and reporting.
Continue to ensure business continuity
Continue to meet your service level agreements by opting for the right appliances to support your business scalability. Solutions provided by Sonic firewall security series can include Global Traffic Optimiser (GTO) supporting intelligent load balancing and support in the area of failovers.
Store sensitive information and data securely
Providing you with onboard memory, the SMA 6200 and 7200 allows for local storage modules, i.e., logs, file transfer inspections, reports, restores, firmware backup, and much more.
Manage user licences better
For companies that operate on a global level, central user licensing through CMS can help to manage the fluctuating demand from users managed SMA appliances, based on their usage.
Sonicwall NSA Firewalls
Sonicwall SMA can fit seamlessly into any existing IT infrastructures, offering users advanced security, secure access to networks, and cloud resources, as well as providing a more centralised approach when providing remote and mobile access.
For further information on the Sonicwall firewall series, contact 0333 2405667 or email enquiries@sonicwall-sales.com, we’d be happy to help!
Read the next article: Blocking pesky apps and multimedia sites using application control
Wireless Security Network KRACKS
Recent flaws in the design of WPA2 found by Belgian security researchers have publicly shown that more and more cybercrime regarding wireless networks is inevitable.
Known as KRACKS, these attacks (also known as key reinstallation) are a profoundly sophisticated attack. Used by cybercriminals to steal private and confidential data from unsuspecting users as they operate through a wireless network, using the flaws found in a WiFi standard to their advantage.
The team of researchers based their findings on CERT, issuing several CVEs to help support and address the flaws identified, as well as acknowledging those who have been most affected have released patches as of this writing.

For further updates and details of the precise vulnerabilities, you can view the research online www.krackattacks.com
Sonicwall Wireless Security
Sonicwall take all new security alerts and cyber threats seriously. The Capture Labs by Sonicwall, in particular, have looked at the vulnerabilities identified within this latest research announcement finding that the SonicWave and SonicPoint wireless access points are not vulnerable.
This is also true for the TZ and SOHO Wireless firewalls.
For all Sonicwall customers, this means that no updates or patches are required for both the integrated wireless and Sonicwall wireless access points.
Ways to protect your wireless network further
To help minimise the risk spouted by this latest cyber threat, we do advise (whether you’re using a Sonicwall global VPN client or not) to follow some of the actions outlined below:
- Ensure all your Wi-Fi clients are patched. Whether this is Android, iOS, Windows, Mac OS, or Linux, make sure you patch them with the latest KRACK updates. (The actual threat does not come from the wireless router but rather from compromising the wireless device, which is important to understand when carrying out patches.)
- If you aren’t a Sonicwall VPN customer, you will need to speak with your client-vendor to find out if a patch on your access points and routers is necessary. In an ideal situation, your Wi-Fi solution would be managed centrally to enable you to place patches more efficiently without taking up too much of your IT team's time. Note: For Sonicwall wireless customers, no updates or patches are required to the routers or access points.
- Look to enhance your security options, adding in additional layers through VPN technology. Encrypting all traffic between wireless devices and firewalls you have in place can protect you two-fold. For Sonicwall customers, we also recommend:
- On mobile devices for SSL encryption, opt for the Mobile Connect from Sonicwall
- Look for the Sonicwall Global VPN client for all IPsec encryption
- Provide updates and policies to users on best practices when sending sensitive data. Ideally, only using encrypted web pages.
- For a specific third radio which is ideal for scanning, the SonicWave series can offer it all. This intrusion detection element allows users to block traffic from unknown routers and access points, ensuring the scanning is continuous and monitoring for all types of threats in real-time.
- For a cybercriminal to commit to an attack, they must be within your Wi-Fi reach, so always lookout for any suspicious activity.
- There is also no requirement to begin changing Wi-Fi passwords and resetting these. This is because KRACKS do not need Wi-Fi passwords for them to be successful.
Sonicwall wireless security is designed to provide users with complete peace of mind. To ensure that your IT systems continue to provide you with continued high-speed access which is secure whether you’re using a wired or wireless network.
Helping you to stop more attacks affecting your networks, Sonicwall’s wireless network security solution helps to provide you with leverage when it comes to identifying and preventing cyber-attacks.
Providing Capture sandbox through a multi-engine, deep packet inspection (including cloud-based applications), as well as a centrally managed SonicWave 802.11ac Wave 2 wireless access points - Sonicwall has a solution to cover it all.
To find out more about the security solutions available to you, call us on 0333 2405667 or email enquiries@sonicwall-sales.com
SonicWall Exposes New Cyberattack Data, Threat Actor Behaviors in Latest Report
For cybercriminals and threat actors, the digital frontier is a lawless panorama of targets and opportunity. Despite the best intentions of government agencies, law enforcement and oversight groups, the modern cyber threat landscape is more agile and evasive than ever before.
For this reason, SonicWall Capture Labs threat researchers work tirelessly to arm organizations, enterprises, governments and businesses with actionable threat intelligence to stay ahead in the global cyber arms race.
And part of that dedication starts with the 2020 SonicWall Cyber Threat Report, which provides critical threat intelligence to help you better understand how cybercriminals think — and be fully prepared for what they’ll do next.
Global Malware Dips, But More Targeted
For the last five years, cybercriminals overwhelmed organizations with sheer volume. But as cyber defenses evolved, more volume was not resulting in higher paydays. A change was in order.
In 2018, cybercriminals began to leverage more evasive and pointed attacks against “softer†targets. In 2019, global malware volume dipped, but attacks were more targeted with higher degrees of success, particularly against the healthcare industry, and state, provincial and local governments.
All told, SonicWall Capture Labs threat researchers recorded 9.9 billion malware attacks* in 2019 — a slight 6% year-over-year decrease.
Ransomware targets state, provincial and local governments
‘Spray and pray’ is over. Cybercriminals are using ransomware to surgically target victims that are more likely to pay given the sensitive data they possess or funds at their disposal (or both). Now it’s all about ‘big-game hunting.’
The report outlines the most egregious ransomware attacks of 2019, while also painting a picture of the evolution of ransomware families and signatures, including Cerber, GandCrab, HiddenTear and more.
Fileless malware spikes in Q3
Fileless malware is a type of malicious software that exists exclusively as a memory-based artifact (i.e., RAM). It does not write any part of its activity to the computer’s hard drive, making it very resistant to existing computer forensic strategies.
The use of fileless malware ebbed and flowed in 2019. But exclusive SonicWall data shows a massive mid-year spike for this savvy technique.
Encrypted threats growing consistently
Another year, another jump in the use of encrypted threats. Until more organizations proactively and responsibly inspect TLS/SSL traffic, this attack vector will only expand.
IoT malware volume rising
From hacked doorbell cameras to rogue nanny cams, 2019 was an alarming year for the security and privacy of IoT devices. Trending data suggests more IoT-based attacks are on the horizon.
Cryptojacking crumbles
In early 2019, the price of bitcoin and complementary cryptocurrencies created an untenable situation between Coinhive-based cryptojacking malware and the legitimate Coinhive mining service. The shuttering of the latter led to the virtual disappearance of one the year’s hottest malware.
What Is Service Co-Termination?
Service Co-termination allows you to adjust the expiration dates of all Service Contracts to expire on the same date. Service Co-termination is provided as a free service to SonicWall customers who have active service contracts. Expired services must be renewed before they can be included.
Services covered in Co-termination
- Comprehensive Gateway Security Suite (CGSS) - CGSS will be shown as the individual services that make up the suite
- Gateway Anti-Virus & Intrusion Prevention Service
- Content Filtering Service - Premium
- Content Filtering Service - Standard
- Dynamic 24x7 Support (all products)
- Dynamic 8x5 Support (all products)
- Capture Client
Services Covered under Zero Pound/Dollar Co-term
- Dynamic 8x5 Support (all products)
- Dynamic 24x7 Support (all products)
- Gateway AV
- IPS
- Content Filtering Service - Premium
- Content Filtering Service - Standard
- Comprehensive Gateway Security Suite (CGSS) will be shown as the individual services that make up the suite
Services not currently covered
- Comprehensive GMS
- GMS SW Support
- CASS
- Email Security
- CDP Site-to-Site
- CDP Off-Site
- Antispam Desktop
- Software & Firmware-only" updates
Services not applicable to Co-termination
- Aventail Support for Advanced Reporting
- ViewPoint
How Service Co-termination is calculated
The value of the selected services in the MySonicWall account is calculated and averaged between the chosen items so that all services expire on the same date.
MySonicWallCo-termination calculates a common expiration date for the selected services in the following way:
- The number of days remaining until expiration is determined for each service (DR).
- The cost per day is calculated for each service (CPD). This is determined by dividing the price of the service by its duration).
- The Days Remaining times the Cost Per Day yields the Remaining Cost of the service (RC).
- The sum of remaining cost of the services divided by the sum of the costs per day yield the Days Variance (DR).
- The Coterm Date is Today’s date + Days Variance.
Coterm Date = Today + DV
DV = Days Variance ( (Sum of RC for all services) / (Sum of CPD for all services) )
Coterm Date = Today’s date + Days Variance
Cost-per-day is the amount a specific service on a specific devices costs for a single day. In terms of co-termination, the cost-per-day for a given service is directly related to the MSRP of the service divided by the number of days in the duration (1 year = 365 days, 2 years = 730 days, 3 years = 1095 days).
 EXAMPLE:
EXAMPLE:
- On the NSA E7500, Dynamic Support services for 1 year cost $4,859. The cost-per-day for Support on the NSA E7500 is:$4,859 / 365 = $13.31
- In comparison, the TZ 150 Unlimited’s Dynamic Support services for 1 year cost $89. The cost-per-day for Support on the TZ 150 Unlimited is: $89 / 365 = $0.24
How Co-termination is performed
- Select the devices and services you wish to modify and click the appropriate checkboxes.
- Click Co-Term Services when you have selected the services to be co-terminated. At least two services must be selected.
- Products can be grouped or filtered by Product, Service Name, Expiration Date, or days until service expiration, allowing you to narrow the choices to the most relevant products.
- After Co-termination dates have been calculated, they appear in the Co-term Date column.
- If you agree to this date, select the checkbox and click Complete. Otherwise, click the Back button to revise the co-termination order.
Co-termination Frequently Asked Questions (FAQ)
What Is Co-termination?
- Co-termination is the process of consolidating many service contracts to produce a common expiration date.
Do I need to buy anything?
- No purchase is needed. SonicWall offers the Co-termination feature free of charge to customers with active service contracts.
How does it work?
- MySonicWall will survey services chosen by the user, calculate the dollar value of the time remaining for those services, then spread that value across the devices so the services all end on the same date.
Can I co-term services on multiple devices?
- Yes. You can co-terminate services on a single device or all the devices in your MySonicWall account.
My company has multiple accounts with SonicWall. Can I co-terminate services for devices in all of them?
- You can run the Co-termination feature only for devices registered to your MySonicWall account. If your company has multiple accounts, you can transfer devices to a single account, then run the Co-termination feature.
How can I coterminate services for only a few select devices?
- Yes. The Co-termination feature will let you easily filter and group your devices. You can explicitly choose which services you would like to co-terminate.
Some of my services have expired, why can’t I select them for Co-termination?
- The Co-termination feature is available only to active services. If a service has expired, you will need to purchase a license and activate it through MySonicWall before it can be co-termed.
A Virtual Firewall that Protects Multi-Cloud Environments
Creating and developing a mix of private, public, and hybrid cloud computing environments is all part of the norm in today’s modern data centres, especially with the increase in virtualisation technology and advancements across all data and network infrastructures.
With research predicting that over 90% of organisations will be running a cloud-based infrastructure by 2024, is your business network security ready for the move to the cloud?

Businesses must be able to expand into this highly dynamic public or private cloud environments, embracing the new technology with open arms or else face the risk of control challenges as well as the risk of online and virtual blind spots!
This is where virtual firewalls are vast, becoming an essential component of a business’s security platform.
Operating together in a way that is easily managed on a day to day basis.
With news and reports hitting the headlines regarding more and more company data breaches, trust us when we say, whether you store your data in a data centre or a hybrid, private or public cloud, ultimately, it is this data that is your hackers goal, and often, they will stop at nothing to get it.
However, securing your cloud platform brings with it a set of challenges within itself.
These challenges can include unpredictable security functionality, a lack of network traffic visibility, and the difficulty in keeping up with the speed of change that cloud environments often bring with them.
To stay ahead of the game and on top of security threats, businesses must look towards cloud security systems that:
- Uses identity to identify and control network traffic, not protocols and ports
- Prevents malware from accessing your systems and moving to different locations in the cloud
- Helps to identify who can use the applications, as well as provide a system of control where access can be granted based on credentials and need
- Gets businesses set up and running in an instant. Streamlining deployment, so you no longer have to configure separate firewalls, saving you time and providing you with a predefined configuration.
- Replaces those outdated and expensive technologies such as WAN connections with cost-effective alternatives. For example, upgrading to the SD-WAN from the MPLS.
- Makes administration much more straightforward. Minimising security policy delays as more and more virtual machines are removed, added, or indeed moved about within your cloud environment.
Sonicwall NSv Virtual Firewall – a firewall you can rely on
The launch of the new SonicOS 6.5.4 firmware, has caused a stir in the cybersecurity market, and for all the right reasons!
With its hardware firewall platform, the new virtual Sonicwall firewall offers numerous benefits to organisations.
Supporting secure Zero-Touch Deployment, SD-WAN, Restful API, DNS Security, and much more – the Sonicwall firewall series has been designed to solve all of the issues identified above and more.
The NSv firewall also supports your security teams by reducing the security risks to your organisation regardless of type and vulnerability, avoiding severe disruption to your business’s everyday operations and critical services to customers.
Additional features include a whole host of security tools and services, including RFDPI (reassembly-free deep packet inspection), security networking services and controls all similar to what a Sonicwall physical firewall can provide.
Ultimately the NSv can effectively shield all of the critical elements contained in your public and private cloud environments.
What’s more, NSv is easily positioned between virtual networks in a multi-user virtual environment.
This means you’re now able to capture all data exchanges and communications between virtual networks aiding you in automated breach prevention, as well as enhancing data confidentiality, providing stringent access control measures, and VM integrity and safety.
This comprehensive security suite also helps to eradicate cross-virtual-machine, network-based intrusions, side-channel attacks, application and protocol vulnerabilities, and more.
Subjecting all traffic through several threat analysis protocols that include anti-spyware and gateway anti-virus, intrusion prevention, anti-virus protection for cloud applications, application control, botnet filtering, and multi-engine sandbox Capture Advanced Threat Protection.
If you’re looking for a security platform to work hand in hand with your cloud-based applications, look no further than Sonicwall.
For further information on how to protect multi-cloud environments further with Sonicwall firewall, visit our website at www.sonicwall-sales.com or email us on info@sonicwall-sales.com
Read next blog: The latest Sonicwall Secure Mobile Access and why you should upgrade
The Ultimate Guide on How to protect your PC from computer invaders
The Ultimate Guide on How to protect your PC from computer invaders

he internet and being online is one of, if not THE, ultimate resources for everyone in today's modern and dare we say it, digital world.
We use it for everything! To communicate with others, to carry out research, to work, to shop, to play etc. - when it comes to the internet the list could go on and on.
It's convenient; it's there at the tip of our fingers, and now with wi-fi hotspots, we’re never really without a connection!
However, we’re also now much more vulnerable to identity theft as well as invasion of privacy.
We leave digital footprints everywhere and putting your data in the wrong place, or the wrong hands can prove extremely costly, to you.
This guide highlights the cyber crimes you need to be aware of, the common challenges that we find ourselves facing daily, and how we can overcome these challenges by making some simple adjustments to how we view and use the internet and its different platforms.
Table of Contents
1. You are not safe online!

Computer invaders don't go away; they just change focus and adapt their attacks to target and break even the most powerful firewalls and antivirus!
1a) Common threats
Some of the most dominant and well-known cyber threats currently out there include:
Ransomware and Malware both used as a tool to carry our targeted threats, infecting computer systems as they go, and costing customers highly.
Data breaches are still one of the most important threats of today. Stealing personal information or company-wide information can lead to identity theft and fraud.
With business data most commonly found to be used for blackmail purposes or indeed to sell on for money.
Distributed Denial of Service attacks (DDoS) - these attacks are driven not only by financial gain, but also by political, ideological, or just bad opinion.
Payment card fraud - be aware of fake companies that show up at the point of sales online to abuse certain transactions, taking advantage of your personal information.
Crypto jacking – linked with cryptocurrency, crypto jacking attacks aim to exploit a computer user's bandwidth and processing power to mine for cryptocurrency. Such attacks can cripple a victim's system by manipulating their processing power.
Phishing emails – the most common form of threats and attacks due to their realism. Phishing emails set out to obtain personal data, hijack accounts, steal identities, carry out malicious activity from your PC and more!
SPAM – spam is often used to gain access to very targeted networks.
1b) Their effects on a PC
The effects all of these threats have on your PC or computer network can be fatal, fatal for the computer.
Depending on the security you have in place, as well as the type of virus/malware, and the expertise of your IT team, it will all depend on whether the hack and virus can be completely removed before any further damage is done.
Making operating systems run much slower than they should or stop working completely is just one effect these types of attacks can have on a computer.
That and all your files can be encrypted and used to access sensitive or personal information, or worse, your computer can be used to do bad things without you even knowing it's going on.
Your computer might also crash regularly, continuously show pop-up error messages, and create problems when trying to connect to secure networks.
This last point is very important for remote employees, because using their personal computers at home, which may be hacked or infected in some way, to log in to their office's private server, can open up more doors for intruders to gain access to!
1c) Staying safe
There are several ways to increase your security online. These include:
Reviewing your online activities – what sites are you shopping on? What content are you posting, and where are you posting this? How safe are the sites you are visiting?
Install the latest antivirus software and firewalls. With free and paid for protection now available, there is no excuse not to protect your PC. (SonicWall online is a great place to help you get started).
Make sure to use a personal private network. This will not only help your antivirus software to further protect your online privacy, but it will also help to hide IP addresses, protect passwords, and keep you anonymous online.
Be aware of the information you share on social media. Especially Facebook, whose business model is designed on using your personal information for advertising and marketing purposes.
Only use secure shopping sites
Use strong passwords (you will read this point a lot throughout this guide)
Delete or clear your tracking cookies. Deleting your online activity means it's harder to follow you and collect personal information about you.
2. Attack of the invaders
With global cybercrime damages predicted to reach $6 billion in costs (annually) by 2021, the online threat is not only real, but it is also continually evolving.
2a) Cybercrime at its worst - stats, history, and challenges to overcome
The second most investigated crime accounting for 50% of crimes in the UK is Cybercrime.
Hackers are invading PCs on average every 39 seconds!
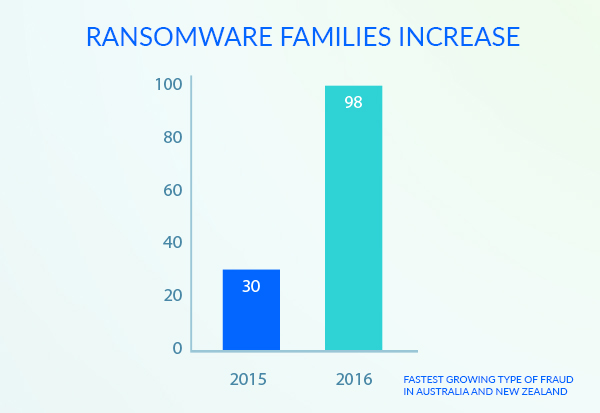
The number of ransomware families has increased from 30 in 2015 to 98 in 2016, with the demand also increasing from $294 in 2015 to £1,077 in 2016.
Records lost to hacking in 2017 stood at an average of 780,000 per day.
2015/16 saw identity takeover become the fastest growing type of fraud in Australia and New Zealand.
In the past year, nearly 200 million people across 21 different countries experienced some form of cybercrime!
The cost of online crime and activity is real:
- The cost of data breaches annually now stands at a staggering $2.1 trillion.
- In 2017, the total revenue coaxed out of people and businesses from cybercriminals worldwide stood at $1.5 trillion!
- $3.8 million, is the cost of data breaches to businesses (on average).
- $600 billion the global cost of cybercrime in 2017.
Challenges come in many shapes and sizes
Take, for example, the recent hacking of Facebook user accounts. Affecting nearly 50 million users worldwide, over 14 million people had their location and search history exposed for all to see!
On this occasion users of the site did nothing wrong and nor was there anything they could do to stop or pre-empt this from happening (besides not having a Facebook account at all), because the hackers took advantage of a Facebook privacy feature, which allowed them to access users' accounts without them knowing.
Now, as one of the largest data breaches in Facebook's history, the company's engineers are working to fix the problem and have advised another 40 million users to log out of their accounts as a precaution. Logging out and logging back in, allowed Facebook to reset users access tokens, protecting their accounts.
Further investigations are still ongoing to the extent of how these bugs can be rectified.
This type of breach is not uncommon as we look further into cybercrime and in particular. WikiLeaks, who released over 8,000 CIA documents (of course classified) in 2017. A team of hackers also released sensitive emails from French presidential candidate Emmanuel Macron in the same year.
Mobile platforms are the fastest growing target areas for hackers, with 80% of mobile fraud carried out through mobile apps and 60% of online fraud carried out through mobile platforms.
These attacks are not only real, but they're big!
3. Keep your computer safe

With online threats at an all-time high, we've compiled a list of top tips to protect you and your computer from computer invaders.
Without needing to install a thing:
- Avoid sites which you don't trust or don't look 100% genuine.
- Don't open emails from unknown/not trusted senders
- Don't open attachments from just anyone!
- Take your passwords more seriously! With more than 60% of people using the same password across multiple sites, make sure you use longer passwords. Use a combination of lower and upper case, numbers, and characters. Avoid obvious ones such as children's birthdays!
- Check your security settings in your browser. Reviewing and setting these at the level that you need and want, you can block pop-ups and irrelevant ads, you can tell websites not to track your location and movements.
- Network security – disabling autorun on Windows, for example, can stop up to 50% of malware threats!
- Wi-Fi security at home – make sure to change your router's default settings by enabling a non-default password and network name.
- Wi-Fi security, public disable sharing and make sure to use a virtual private network (VPN) to secure your data and hide your IP address.
The need for software installation:
- Install the right firewalls and antivirus software depending on your needs and configuration settings required. Also, make sure to keep your firewall turned on!
- Keep your Windows operating system up to date, checking for the latest security updates and patches. Make sure you turn on the automatic update feature.
- Install antivirus and anti-spyware software. Providing real-time protection, helping to identify and block any unwanted mail and threats.
- Look to invest in cloud software or external hard drives, backup your folders regularly, and make sure you have a backup plan if the worst were to happen.
4. Firewalls
Most firewalls, over the years, have been developed in response to a security threat received. Action was then taken to develop and produce more advanced firewall technology to stop the threat from happening again.
4a) How they work
When we think of firewalls, we need to think of them as invisible walls, in both directions, that monitor everything that passes through them. If a threat is found, the wall will not allow it to pass through.
A firewall will ultimately stop hackers from accessing your computer via Wi-Fi connections and the internet and can help in two ways:
- It can allow traffic to pass through, except for data that meets a predetermined set of criteria.
- It can stop all traffic unless it meets a predetermined set of criteria.
Firewalls are a piece of security software that keeps track of the traffic to and from your computer. They are the first line of defence to protect your data and any important information.
4b) Why do you need them?
It is this misuse of confidential information and stealing of personal data which is why we need firewalls.
For example, hackers use Trojan viruses and key logging software to access computers and data. Things like passwords, bank details can all be taken and used without you realising for days (if not longer), racking up huge bills in your name as they go.
They can also use your computer against you, taking complete control without you knowing, and using it to run illegal activities online, or it's affecting the system in any way.
Firewalls and upgraded firewalls like SonicWall firewalls help to stop this from happening, placing a barrier between you and the hackers.
4c) Best Practice
Firewall best practice when it comes to business is to install complex firewall software to protect the most extensive networks, so that such security measures can be managed by a team.
Helping to:
- Prevent staff from sending certain types of emails or transmitting sensitive information.
- Stop employees accessing certain sites
- Prevent outside computers accessing computers inside the network
- Provide a variety of configurations
When it comes to firewalls for personal use, we recommend keeping it simple. The primary goal is to protect your computer and private network from malicious activity.
5. Antivirus software

Anti-virus software, in its purest form, protects against different types of malware, protecting your PC and your personal information.
5a) How they work
Good antivirus software helps to block everyday threats by finding them before they reach your computer, and before they reach you directly, pulling them away, and locking them in a safe place.
Anti-virus software is similar to anti-spy software in that it provides real-time protection (if you make sure to keep it updated regularly). Scanning all incoming information and blocking any unwanted information or threats which it detects.
5b) Why do you need them?
Malware and malicious software attacking our PCs are one of the biggest online threats.A virus of any kind can be spread over the internet and through email, quickly causing damage to your computer and files.
Malware in this sense also includes Trojan Horse programmes and spyware; all used to acquire your personal information for identity theft and fraud.
The right antivirus software will help to prevent spyware and malware from getting onto your computer and invading your privacy, but it is important to set up and use a secure password. Using long passwords including a combination of numbers, special characters, and upper- and lower-case letters is most recommended.
5c) Differences between firewalls and antivirus software
Both developed to offer you and your PC increased security, the key differences between antivirus software and firewalls are:
- Anti-virus can only be implemented in software, whereas a firewall can be both hardware and software.
- Anti-virus performs continuous scans on the PC in question, detecting, identifying and removing any threats found, whereas firewalls monitor and filter incoming and outgoing information.
- Anti-virus software can deal with external and internal attacks, while firewalls can only deal with external.
- You can apply set rules to firewalls for monitoring and securing PCs and networks; this is not possible with an antiantivirus that will run regular checks to see if programs or files are dangerous.
- A firewall can prevent untrusted and unauthorised applications from gaining access to your computer, but it does not do anything about it. Antivirus programs do this for you.
6. Email Security Software

When it comes to protecting your PC and computer systems, you need to make sure to invest in the right security software for you and your PC. However, you also need to bear in mind the need to defend yourself against all known and emerging viruses and hacks.
6a) Integrated email security software
Attacks are getting more and more advanced and varied, and for this reason, integrated email security software should be chosen instead of managing a number of different software systems.
Making life easier An integrated platform means you can manage, control and contain everything through one application. You can monitor all incoming and outgoing activity quickly and efficiently, and you can have a bird's eye view of the security of your PC.
Managing multiple applications is not only a minefield, but because they are all designed to do different things and not talk to each other, security processes can become slow and complicated.
When considering an integrated email security package, look for one that can protect against malware as well as spam, phishing, potential data leaks and more!
The SonicWall email security and sensitive data detection solution can help. Deployed as a software or virtual appliance, this security system gives you complete peace of mind that your computer and operating system are protected.
7. Advanced internet protection technique

In this final chapter, we want to let you in on some of our tips and unique techniques over the years to increase the security of your computer.
Tips that we've never shared before.
7a) Keep things up to date!
Now before you think, you've heard all of this before, and there is nothing left to say on the matter, give us a second!
Yes, when we say keep things updated, we're talking about things such as updating and keeping the latest version of Microsoft - and yes, we know not everyone likes it, but it will help to add another layer of security to your PC.
But, what we also mean is that it's also important to keep the more uncommon elements like your routers and Java up to date too.
Java is something that most of us don't really know to update in the first instance, let alone do this regularly, so it's important to know more about it.
In your start menu, search for Java, clicking and bringing up the Java Control Panel. Any updates and new updates will then be available by the click of a button in the bottom right-hand corner of the panel.
Within this section, we'd also recommend clicking on the security tab at the top and disabling, the Enable Java box.
Why?
Because this is notorious for vulnerabilities and opens up more opportunities and threats than adding additional security.
When it comes to routers, keep these up to date by changing passwords asap, and follow this up with disabling WPS, or Wi-Fi Protected Setup.
Why?
Because if we're 100%, honest WPS is really shaky on the security front!
7b) Change your controls
Most computers and PCs will automatically be set up with you as the administrator with admin privileges and the ability to access everything without question.
Herein lies the problem.
In your control panel, make sure to switch your privileges from admin to standard.
Why?
Because if a virus or piece of malware does accidentally find its way onto your PC, being set up as admin will give the invader the same privileges that you have, and you don't want that to happen.
7c) Keep some things to yourself!
In an era where 2.77 billion people around the world use social media, (an estimated 2.77 billion people around the world use social media), we tend to give too much away about ourselves, our family, and our lives in general.
Stop.
Let's keep some things under wraps, as not placing yourself in a vulnerable position will only strengthen your security position when online fraud and identity theft occur.
7d) Quick-fire tips
Make sure your antivirus software offers real-time protection.
Be aware that even the most trusted websites can be compromised.
Back up everything. Using both local and online backup systems. and
Sign out of things before closing everything down!
Conclusion
Computer invaders are not going away, but being armed with the right tools and information can keep you and your PC protected.
If you enjoyed reading this guide, please feel free to share and comment below with any questions or insight you might have when it comes to computer invaders; we'd love to hear from you.
Spear-Phishing Attacks Targeting Office 365 Users, SaaS Applications
Over the course of the last 15 years, cyber threats have gone from urban myths and corporate ghost stories to as mainstream as carjackings and burglaries. There isn’t a business owner of a small restaurant chain or a CEO of a Fortune 500 company who doesn’t think about the fallout of being breached.
I’m not here to tell you how the threats are getting more sophisticated, or how state-sponsored hacker groups are getting more and more funding; you already know that. But what I do want to share with you is something that I’m seeing daily. Targeted threats that you may have already witnessed and, unfortunately, been personally a victim of or know someone who has: Spear-phishing.
Are you an Office 365 user? Do you have customers who are Office 365 users? Are you a managed security service provider (MSSP) that administrators Office 365 for your clients? You probably need a solution that applies effective Office 365 security capabilities and controls.
With close to 200 million global users, Office 365 is a target — a big target. And spear-phishing attempts are good. Really good. Recently, Forbes ran a summary of the threat. Alarmingly, today’s most advanced spear-phishing attempts look like they come from your CFO, boss or trusted vendor. They provide credibility to the target and, many times, users take the bait. Money gets wired. Access to accounts are provided. Confidential information is exposed.
Traditional email security isn’t enough protection. Out-of-the-box, cloud-native security services aren’t enough protection. A lean, effective and modern Office 365 security or SaaS security solution is required.
How to stop spear-phishing attacks, advanced cyber threats
SonicWall Cloud App Security (CAS) combines advanced security for Office 365, G Suite and other top SaaS applications to protect users and data within cloud applications, including email, messaging, file sharing and file storage. This approach delivers advanced threat protection against targeted email threats like phishing attacks, business email compromise, zero-day threats, data loss and account takeovers.
CAS also seamlessly integrates with sanctioned SaaS applications using native APIs. This helps organizations deploy email security and CASB functionalities that are critical to protecting the SaaS landscape and ensure consistent policies across cloud applications being used.
Explore the five key reasons CAS may be able to protect your organization from spear-phishing and other advanced attacks.
- CAS delivers next-gen security for Office 365, protecting email, data and user credentials from advanced threats (including advanced phishing) while ensuring compliance in the cloud
- Monitor SaaS accounts for IOCs, such data leakage, account takeover, business email compromise (BEC) and fraud attempts
- Block malware propagation in malicious email attachments and files, whether they are at-rest or traversing a SaaS environment, internally or cloud-to-cloud
- Prevent data breaches using machine learning and/or AI-based user profiling and behavior analytics for incident detections and automated responses
- Leverage Shadow IT to monitor cloud usage in real time, and set policies to block unsanctioned applications
In my over 10 years of observing various attacks and sitting in rooms with customers (not mine, fortunately) who have been breached, I can tell you that you don’t want it ever to be you or your customers. This threat is having more success than any I’ve seen — and they are very recent.
For more information explore the CAS solution in detail.
The Ultimate Sonicwall Cybersecurity Support
With the latest Sonicwall TZ Firewall now available, is now the time to upgrade your systems and networks?
Firewalls are one of the most commonly used pieces of software for businesses and individuals. Helping to protect against a whole host of cyberattacks, as well as malware, ransomware, and even encrypted threats.

As cyber threats continue to grow in their sophistication and presence, firewalls must be updated regularly to keep abreast of all new developments.
In this post, we take a look at the top 10 reasons to upgrade your Sonicwall Firewall Support
1. Protects against the most advanced cyber threats
As we’re aware, cyber threats are on the rise with no signs of slowing down. The Advanced Threat Protection sandbox service provided by Sonicwall Captures cloud-based multi-engine offers the highest security levels. Protecting businesses from advanced online security threats as well as new attacks, malware, ransomware, and any side-channel attacks. Thousands of attacks have been discovered and stopped in their tracks by Capture ATP.
To check which firewalls, Capture ATP is suitable for contact Sonicwall support for further information.
2. Supports faster wi-fi speeds
People want things faster than ever before. With everything to be provided wirelessly. However, you need to find a compatible firewall to keep everything secure while also supporting this increase in speed. Ideally, you need a firewall that works well alongside the 802.11ac wireless requirements and standards.
The TZ350 and TZ400 support these standards and more. The SonicWave 802.11ac Wave 2 also provides access points for wireless networking at high-speed too!
3. Keeps performance high while inspecting an increase in encrypted traffic
With SonicWall, system and network performance are no longer affected or slowed down as you begin to build and add more networks, and security remains the top priority.
Allowing more businesses to operate with greater capacity, higher performance rates, increased internet speeds, and further support all users.
4. Keep your remote workers secure
More and more organisations are offering workers the opportunity to work remotely, which also means providing remote access to data. This needs to be kept safe. VPN connections, therefore, need to be secure and often depending on the firewalls you have in place will depend on how many remote employees you can protect at any one time.
With the TZ400 firewall from Sonicwall, your business can support and protect ten times more SSL-VPN clients!
5. Keeping costs competitive
You will now find a high percentage of encrypted web traffic filtering through systems, which is great for individuals and companies, not so great for cybercriminals. That’s why we’re now seeing an increase in cybercriminals looking to attack through the backdoor of your network.
Sonicwall support understands that deep packet inspection of all encrypted traffic is required by all businesses, regardless of their size. But what makes our products different is that we don’t charge more for you to have the most appropriate and adequate TLS/SSL capabilities. For example, the TZ350 and TZ400 Sonicwall firewalls have the highly sought after DPI-SSL licence by default, providing this to consumers at no extra charge.
6. Increased memory for additional users
As the number of users on your network grows, so should your level of protection and security. Unfortunately, some older firewalls can’t support every user across the network. However, the latest Sonicwall Firewalls offer more onboard memory allowing more users, policies and rules, as well as log messages to be stored. Reporting is now also much more accessible, as organisations protect and empower a much wider user base.
7. Protect more users
With the new Sonicwall firewalls, you can achieve greater scalability, allowing more active users to be protected simultaneously, removing the barrier on how many users you can protect at one time.
8. Keep your support costs low
Providing a single ID and password to help users gain access to networks safely and securely, you can maximise the use of single sign-in advances in technology - helping to reduce associated IT costs and increase workforce productivity. With Sonicwall TZ350 and TZ400, these firewalls can benefit double the population of users, all from the use of a single sign in.
9. Faster speeds
With the latest updates and upgrades available, you can now increase network traffic through our systems as well as offer a higher level of performance linked to threat processing.
10. Enhance security and performance with extra VLANs
Being able to segment users and devices into more targeted groups through a greater number of VLANs helps to reduce the cost of hardware and improve security and performance. Upgrading to the TZ400 will allow you to increase the number of VLANs five times over, with the TZ350 allowing you to create up to two and a half more.
Sonicwall Online
For integrated security solutions that are flexible and operate at high-speed, look no further than the TZ series from Sonicwall.
Tailored to meet all of your specifications.
Stay protected at all times, contact Sonicwall firewall support on 0333 2405667 to find out more.
How to create a professional cold email without going to recipients spam folder - The Ultimate Guide
How to create a professional cold email without going to recipients spam folder - The Ultimate Guide

At some point in our career lifetime, we have sent out or indeed been sent a cold email.
Those emails where there is no relationship as such with the sender, and you are introducing yourself for the first time. Cold emails are still to this day, the most effective way for businesses to increase their lead generation.
But, and there is a bit, these emails need to get through the numerous security filters and settings that businesses now operate.
Sometimes, you can have the world's best content inside those emails, but ultimately it comes down to whether your email will be a success or a failure.
Many things now need to be considered when sending out cold emails and this guide will show you not only how to create an expert cold email, but how to make sure it doesn't end up in the spam folder of the recipient.

Contents Covered
1. A guide to cold emailing
a. How to successfully land in someone's inbox
b. The most important dos and don'ts for cold emailing
c. Tips for producing compelling content
2. Cold emailing deliverability
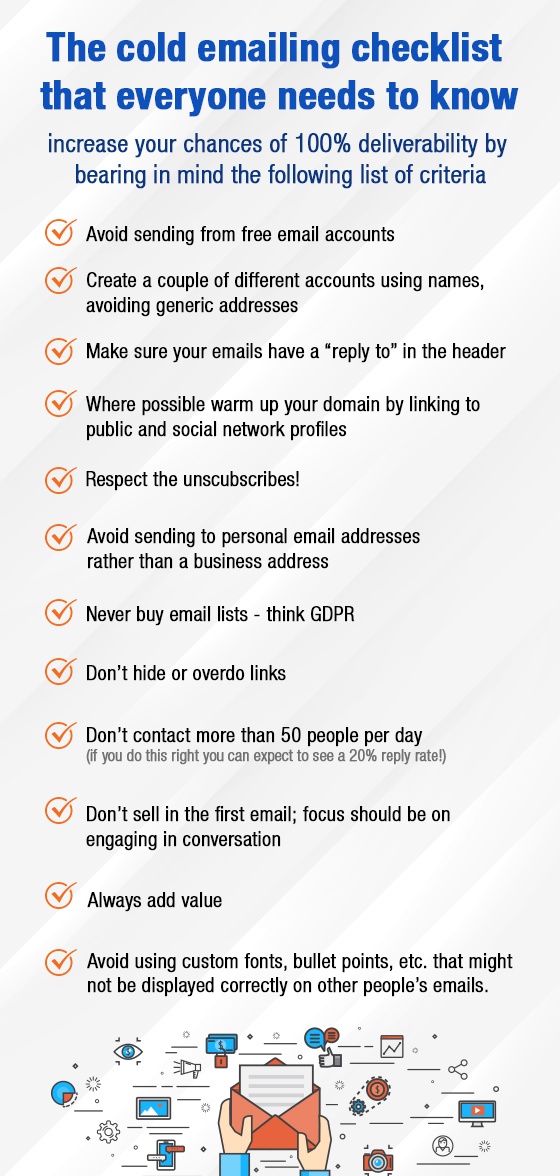
d. The cold email checklist everyone needs to know
3. Red flag
e. Need to show them you're human
f. Avoid similar content
g. Spam filters pay attention to things out of the ordinary.
h. No groups, only individuals
4. Spam emails
5. Your ultimate email security guide
6. Technical attacks
i. Viruses
j. Phishing attacks
k. Denial of service
7. Email encryption
l. The benefits
m. Encryption should be...
1a. A guide to cold emailing and how to successfully land in someone's inbox
There is no definitive way to successfully land in someone's inbox and make them read your email and then act upon its content.
But, in this chapter we will explore some of the tried and tested tips which can increase your chances of making this cold email a more successful one.
Starting with, make it personal. Most marketers and content writers will stress this in all sales approaches, but to make it clear, you need to tailor the message to the person you are sending it to to be successful.
Of course, this is harder than usual as you have no relationship with this person or feedback, etc, but it can be done. Research them, check out their LinkedIn profile, what interests them, what news is the following, how do they see the specific niche that they are specialising in, and what is it that they want?
You need to show them that you have put the work in. Make them feel special and not part of a cold emailing campaign where everyone has received the same message. Tell them why you are emailing them as opposed to anyone else, where do they fit in with your thinking etc.
Tell them about yourself. No boasting here, but you need to show them that you're credible and that they can trust you. Do you have any direct connections or mutual friends, similar groups that you are part of, etc.? The aim here is to make it, so you don't feel like a stranger to them. Remember we're told from a very young age not to talk to strangers, so you need something compelling to change this.
Identify their pain points and give them something they want. Why should they care about your email? What are their pain points? Make them appropriate and relevant to your content and the offer that you are providing them with.
Keep emails to the point and actionable. Research has shown that short emails are more likely to be read than long ones. People who ask for specific action will also get a higher response rate.
If you have a point in the email, get to it. And if you want the recipient to do something, tell them what that is. Try to avoid getting them to choose as this involves thinking and processing, which consumes too much time.
Say thank you. Being appreciative as well as showing a little bit of vulnerability provides recipients with the feeling that they're a good person if they help. Of course, it also gives them power and status too.
Finally, don't use templates and write the email as if you were giving a speech. If the email when read aloud doesn't flow smoothly, then change it.
1b. The most important do's and don'ts for cold emailing
For your email to be perfect 100% of the time, there are a few dos and don'ts to take into consideration when constructing your approach.
Do
- Target smartly: don't just email anyone, focus on whom you want to connect with, building a lead list and an understanding of your audience.
- Segment! You will be guaranteed to receive a higher click-through rate if your target audience is segmented appropriately, customising your pitch. (Look to segment by industry, title, location, company size, products of interest, etc.)
- Have a compelling subject line. This is the reason why they choose to open it or not. It should convey a fantastic benefit or spark some curiosity. Short to the point and ideally five words and under.
- Use the right sender name. Make sure to send the email from an actual person, not marketing@ for example; you will receive a much higher click-through when its person led.
- Split test everything. Test the length of your emails, the Call to Action, colours used, times sent, subject lines, how links are formatted, tone of voice, tracking links and more!
Don't
- Include too many pictures. Look to abide by the 80: 20 rule when it comes to text to picture ratio, especially as spammers are known to hide links in pictures, hence most security filters will reject emails with too many!
- Rush to close your prospect. Remember, they don't even know you. You need to build up trust and a rapport, dig deep, build a relationship and then go for the sale kill.
- Send all your cold emails all at once. This will only have them targeted as spam, pacing them at 20-30 second intervals between every send helps to avoid this trap.
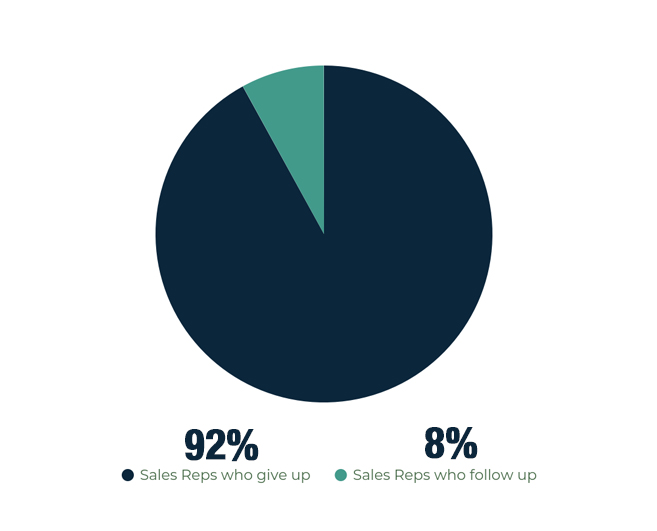
- Forget to follow up. Reports show that 80% of sales require at least five follow-ups after initial contact. However, 92% of sales reps report to give up before then, with the 8% that carry on following up, closing 80% of sales.
- Make follow-up emails generic. Make sure to inject a bit of humour where possible and keep things light-hearted; remember you're looking to build rapport.
- Track links. Tracking links within emails will increase your chances of hitting people's spam filters.
1c. Tips for producing compelling content
Content is what sells people, products, places, services and more. It's what we use to engage audiences with and get them to follow through on what we want them to do. This section looks at some top tips when it comes to creating such compelling content.
Mentioned earlier in this guide, is the point that within cold emails you need to communicate that you understand their pain points, and what you're going to tell them will help alleviate this, and what problems they/ there sector is facing.
Reminding them about the problems compels readers to read on, as they find common ground with someone who knows and shares their pain.
In some cases, research on cold email content has shown that if you raise these issues a little further, then swoop in with a solution, a positive result is more likely to follow-up with a call to action.
However, make it their decision. Make sure that they know that they are in charge. For example, if you would rather not, I fully understand and thank you for taking the time to read this email so far. This type of psychology doubles the chances that they'll say yes!
Content creation is about telling a story with a successful outcome at the end. You want to grab their attention, engage their interest, build a desire for your products and services by telling them about the facts, your big ideas, and the proof points. You ask them for a direct response, and you hook them with a strong call to action.
You will find that the most successful cold emails are fact-packed ones, those that are concise, specific, contain few adjectives and overall spark curiosity.
In a switched-on digital world, no one has time any more, so you need to make sure you get to the point.
We're not re-inventing the wheel, but instead using combinations of tried and tested formulas within our business contexts.
2. Cold emailing deliverability
Writing compelling content for an email to be read is one thing. Making sure it is delivered into the intended recipient's inbox is quite another.
With email security higher than ever, how can you ensure your emails are delivered correctly?
Firstly, and one which not many people are aware of, don't the very first cold email using your primary domain. Make sure to purchase a few domains that relate to your primary address, for cold email campaigns. This way, spam filters will not find your primary address.
It's also recommended that you avoid using.com where possible as these are also email addresses that are more likely to be checked by security software.
Secondly, check your email list. When 6-8% of the emails you send start bouncing, it will affect your overall email deliverability, with email providers soon blacklisting you across different platforms (see why we recommended buying alternative domains at the very beginning).
Check the details you have and the data you house, as well as monitor the bounce back rate when you start receiving emails in return.
Thirdly, you can check your deliverability using services such as mail-tester.com, taking their recommendations and working with the results you are then sent.
3. Red Flag
So, what constitutes a red flag when it comes to cold emails? What factors do they raise and how can we overcome them?
3.a. Need to show them you're human!
This is important, because email security software and spam filters can be very tight. If your email is thought to be spam, it will go through spam filters and never reach its intended destination.
A red flag in this area is when emails are all sent at the same time, without the time lag in between, this can show you as a spamming machine rather than a human being.
Make sure to pace your emails with 20-30 seconds between each send. Tools such as Mix max, Yesware, and Mail shake can all make it easier to send cold emails. They also give you advice on how to make your emails work better. (These platforms can also generate sending out emails through your Gmail accounts too).
3b. Avoid similar content
All content in your emails should be unique, but we tend to take advantage of commonly used words and phrases in the industries we work in.If you are sending out cold emails similar to content that is already out there or indeed like the content you have already sent (think about your follow-up emails), this will be followed-upgged and end up in spam folders or deleted altogether before even being read.
The key is not to repeat yourself; create unique and compelling content.
3c. Spam filters pay attention to things out of the ordinary
Things like additional links in the text or hidden in pictures. They also raise a red flag for shortening links.
In this case, it's important to write links in your email without making them a clickable link, or indeed disable link tracking systems. This will make it much easier to pass through spam filters.
3d. No groups, only individuals
Make sure when checking your email lists there are no group email addresses mixed up in there. Things such as finance@, sales@, etc as emailing these will again raise red flags and report your domain address as spam for any future communications.
4. Spam emails
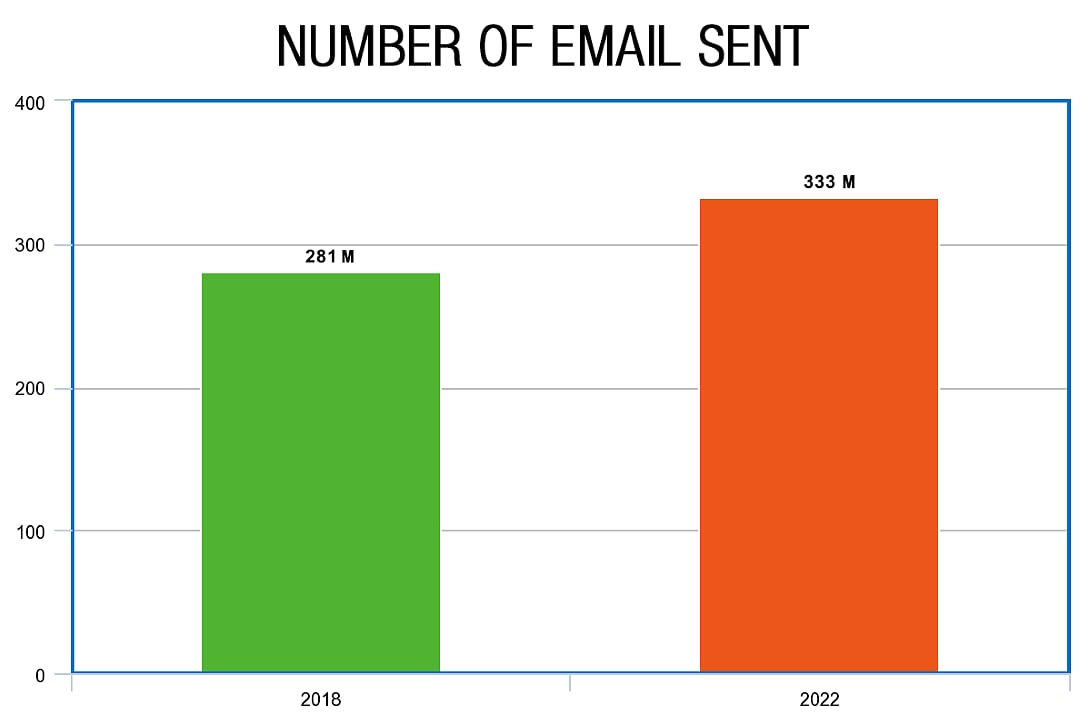
With studies showing that over 281 billion emails were sent in 2018 and about 333 billion could be sent in 2022, email plays an important role in business and society.
Knowing how email works is ultimately how we develop our understanding of spam emails as well as being aware of potential threats and IT attacks.
Email is ingrained in how we communicate, sell, inform, and develop. Offering us the opportunity to communicate with anyone, anywhere at any time. They are simple in nature, so everyone who encounters them understands how to use them.
However, messages and information are openly exposed to others and just because we can't physically see it doesn't mean this exposure isn't happening.
For example, emails can be intercepted, read, edited or even have viruses and malware placed within them, before being passed on to their final recipient.
For example, public networks mean just that!
Sending mail via public networks means that an email is visible to anyone. It goes through other people's servers to get to where it is going, and the people who run these servers can quickly stop it, do something with it, and then send it on its way.
The temptation of knowing what is sent in an email is too much for hackers; the temptation of knowing what is sent in an email is too much and placing something untoward in the email causing problems to the recipient.
5. Your ultimate mail security guide
There is a growing threat of hackers, viruses, spam emails, identity theft and phishing, as the number of people using email has increased dramatically.
So, how can you secure your business and keep your information safe?
Email security
When it comes to email security software and systems, this is often multi-layered, with several types of security technology now available.
Using things like spam filters, software that can scan email attachments (9 out of 10 viruses that infect a computer and network come from attachments), as well as relying on resources such as Microsoft eExchangeserver hosted encryption, can all help to increase email security. For example, Sophos PureMessage for Microsoft Exchange can scan all email messages.
Good network security systems
Private network security systems within the business increase email security as well as check for spam and phishing emails coming in through a secure server.
It's important to consider introducing instant messaging protection, email spyware protection, personal firewall tools (some of which will come with operating systems and then with add-on security suites), as well as identity protection and content blocking, which helps to prevent viruses and malicious content from getting into the computer system.
Good communication and training
Communicating and training staff in email security is key. Knowing what to look out for, and the signs of an unsolicited and potential spam email, is essential to embedding into the company culture.
Building email policies and best practices to include things such as:
- Don't open emails from unreliable sources
- Don't click on web links within emails
- Be careful when clicking on reply all within emails, as well as using the forward function
- Make use of the bcc
- Have strong passwords, which are never shared and updated regularly
Make sure you have the appropriate compliance controls in place so that you meet the legal and regulatory compliance requirements surrounding emails and email security.
6. Technical attacks Viruses
Viruses come in many forms and from several different sources, affecting computers and systems in different ways. Viruses are a way to install malware or malicious software onto your computer to delete information, steal data and information, even hold information and you hostage!
Time-consuming and annoying, viruses can take a painstaking process for them to be entirely removed from your machines and networks.
The best way to counteract viruses is to include anti-virus filters, filters which remove infected and potentially infected emails from the system before an employee even has a chance to open it, let alone click any links or attachments.
6b. Phishing attacks
Phishing attacks are a way for hackers and spammers to target users to try and get them to hand over and enter personal details. Usually entered onto a fraudulent site, phishing emails are much more sophisticated now than a couple of years ago, looking authentic in appearance and with many passing through email security and antivirus settings.
It's important to look at your email filtering services and train employees on how to spot a potential phishing attack and what to look out for in a phishing email.
Protecting customers, employees and your business from the latest phishing attacks out there is vital to protecting your personal and company data.
6c. Denial of service
This is independent of human error and designed to overload the company's mail server with incoming mail and attachments. A DoS attack is both an inconvenience and time-consuming; however, if it does happen, it's important that you base your email security over multiple data centers.
7. Email Encryption
Email encryption is used to protect sensitive information sent in emails. Encryptions services can help protect both the sender and the recipient. Depending on the type of encryption used, it can be very difficult to break because the code is very complex.
7a. Benefits of email encryption
Mitigates risk
Human error is inevitable. Sharing information publicly when it's a private document, forwarding the wrong email to the wrong person, and sharing attachments that shouldn't be shared are all bad for your business.
Using encryption software helps to mitigate these risks and problems, as it allows you to control information much more carefully.
Control information contained within emails by being able to set time limits before emails automatically expire, disabling forward options so that emails can't be passed around, and having recall functions if emails are sent by mistake.
Controls access
You can control access at each stage of your email journey, showing who has access to your content, who has received it and if so who, etc.
Ultimately you are in control, and you can always remain in control.
Don't always have to remember
Integrating email encryption into your IT solutions can make sure that employees don't have to continually remember how to encrypt sensitive information or protect email attachments, as this will be done for them as part of their operating system and they will not have to remember how to do it.
7b. Email encryption should
- Be effortless
- Be universal
- secure any file attachments
- transport sensitive information securely
- remain private!
Without email encryption, your email messages and attachments remain unprotected.
Conclusion
Cold emailing plays a vital role in business development and networking. Making the right email, with the right information, and using the right software approach can ensure that the email is actually read by the intended recipient, and not just spam.
If you have any questions you'd like to ask, maybe you'd like to share your email security experiences with us, or if you feel something is missing from our guide, we'd love to hear from you! Comment in the box below or email enquiries@sonicwall-sales.com
Read related post: Everything You Need to Know About Log4j
10 Reasons to Upgrade to the Latest SonicWall NSa Firewall
Firewalls are the workhorse of network security and are especially adept at mitigating advanced threats like malware, ransomware and encrypted threats. Firewall appliances must, however, be regularly upgraded to stay ahead of cybercriminals.
Still running an older SonicWall NSA or E series model? Consider these 10 reasons to upgrade to the latest mid-range SonicWall NSa next-generation firewall.
Stop the Most Advanced Threats
Advanced persistent threats move with great speed and veracity, and are designed to target and infiltrate all businesses and organizations.
However, a cloud-based, multi-engine sandbox, such as the SonicWall Capture Advanced Threat Protection (ATP) service, provides real-time security against advanced cyberattacks, including ‘never-before-seen’ ransomware, malware and side-channel attacks. Each day, Capture ATP subscribers discover and stop more than 1,000 new attacks each business day.
Why upgrade: SonicWall Capture ATP is only available for the NSA/NSa 2600 and newer next-generation firewalls, as well as the current TZ and NSsp product lines (sixth generation or newer). This service is not available for legacy SonicWall firewalls, including some NSA and E Series models (usually silver in color with the old blue SonicWall logo).
Inspect Traffic without Slowing Performance
You should never be put into a position to choose between security and performance. With bandwidth-hungry apps woven into our everyday lives — SaaS apps, video streaming and social media — firewalls with faster deep packet inspection (DPI) are better at securing networks without greatly affecting performance.
In fact, through the first three quarters of 2019, SonicWall registered 3.1 million encrypted attacks. This marked a 58% year-over-year increase from 2018.
Faster DPI performance gives businesses greater capacity to utilize higher internet speeds and support more concurrent users without ever sacrificing security.
Why upgrade: For example, NSa 2650 delivers a 25% DPI-SSL performance improvement over the NSA 2600. SonicWall NSa 2650 and newer firewalls (e.g., 2650-9650) offer significantly faster DPI performance than their predecessors, the NSA 2600-9600 range, E Series models and other older appliances.
Inspect TLS/SSL Traffic without Increasing Costs
The majority of web traffic is encrypted today. Without proper security controls in place, TLS/SSL encryption standards provide cybercriminals easy access to your network.
That’s why deep packet inspection of encrypted traffic (DPI for TLS/SSL) is mandatory. Some firewall vendors, unfortunately, upcharge for proper TLS/SSL inspection capabilities or simply don’t offer the capability at all. Unfortunately, inspecting TLS/SSL traffic also takes compute power and organizations need a firewall that can process TLS-encrypted traffic without hurting performance.
Why upgrade: The latest SonicWall NSa firewalls include the DPI-SSL license (by default) to inspect encrypted traffic at no additional cost, thereby reducing capital expense. Unfortunately, older-generation NSA firewalls (usually silver in color with our old logo) do not support inspection of encrypted traffic.
Expand Remote Branch/Site Security
For organizations with remote and branch locations, such as retail POS businesses, the ability to create a larger number of site-to-site VPN tunnels to connect distributed networks together and securely share data is essential. But not all firewalls have the capability or capability to make this happen.
Why upgrade: By moving to the latest NSa firewall series, your organization can secure more remote branches, services and devices. This is particularly powerful for distributed enterprises, retail organizations, etc. The NSa 2650, for example, enables the creation of 4x more site-to-site VPN tunnels than the NSA 2600 (1,000 vs. 250).
Support More High-Speed Wi-Fi Connections
Fast and secure Wi-Fi is a requirement in today’s hyper-connect world. Today’s wireless standard, 802.11ac, delivers the performance, range and reliability of high-speed wireless technology for a safe and fast user experience.
In a properly secured environment, wireless access points must be paired with a firewall that can support 802.11ac wireless standards.
But newer firewalls can support more connections, too. The option to connect a larger number of wireless access points to a single firewall enables organizations to extend their wireless network farther without purchasing additional hardware.
Why upgrade: Combine the latest NSa series next-generation firewall with a SonicWall SonicWave 802.11ac Wave 2 wireless access point to create a high-speed wireless network security solution.
NSa series firewalls and SonicWave 400 series wireless access points both feature 2.5 Gigabit Ethernet ports that can support multi-gigabit wireless throughput, which is available in the 802.11ac Wave 2 wireless standard. In addition, you can connect more wireless access points to the latest NSa firewall. The NSa 2650, for example, supports 1.5x the number of connected SonicWave wireless access points as the NSA 2600 (48 vs. 32).
Unfortunately, legacy NSA and older firewalls (as well as those on SonicOS 5.x or older firmware) do not offer multi-gigabit ports to accommodate the faster throughput supported by Wave 2 wireless standard.
Decrease Support Costs
Single sign-on (SSO) technology helps secure your environment, as well as employees, to be more productive and helps shrink IT support costs (e.g., tickets, calls, etc.) by enabling users to safely gain access to connected systems with a single ID and password.
Simply, the more users who can access a system with a single ID, the fewer support calls, IT tickets and complaints that will be generated. This self-service approach means real savings to your business or enterprise.
Why upgrade: The NSa 2650, for example, allows a larger population of users
(40,000 vs. 30,000) to benefit from the use of SSO compared to the legacy NSA 2600. This disparity widens the further you go up the product line.
Increase Network Capacity
With increased network bandwidth requirements from apps, video streaming and social media, faster DPI and DPI-SSL performance provides a secure network without performance degradation.
Faster DPI performance also provides organizations with a greater capacity to utilize higher internet speeds and support more concurrent users. A higher number of concurrent connections provides greater scalability by enabling more simultaneous user sessions to be active and protected by the firewall.
Why upgrade: The NSa 2650 enables 500,000 deep packet inspection (DPI) connections and up to 100,000 deep packet inspection of TLS/SSL-encrypted (DPI-SSL) connections compared to the 250,000 for
DPI and 1,000 for DPI-SSL on the NSA 2600 and older models, such as the NSA 220 (32,000 for DPI).
Boost Memory for Added Users, Logs & Policies
The number of users who require security on your network grows by the day. Unfortunately, the on-board memory of legacy firewalls can only support a finite footprint of users on the network.
Advanced NSa firewalls offer more onboard memory to allow for more rules and policies, users and log messages to be stored on the firewall, making reporting easily accessible.
Why upgrade: The NSa 2650 has twice the onboard memory of the NSA 2600 (4 GB vs. 2 GB) and eight times the memory of the NSA 220 (4 GB vs. 512MB). This increased capacity empowers organizations to use a single NSa firewall to protect a larger userbase with deeper and more robust rules and policies.
Ditch the Switch with More Ports
It’s time to clean up your server room or IT area. Having a greater number of ports allows organizations to connect more SonicWall devices directly to the firewall without needing to purchase a switch. In addition, organizations that require increased throughput to support bandwidth-intensive applications and data transfer need multi-gigabit ports.
Why upgrade: Newer NSa firewalls offer many more ports than their predecessors. For example, the NSa 2650 has 2.5x the number of ports as the NSA 2600 (20 vs. 8). The NSa 2650 also features eight 2.5 GbE ports while the NSA 2600 has none.
Improve Business Continuity
Many enterprises and larger organizations build in businesses continuity and disaster recovery plans in their process. Part of this is planning is ensuring there’s a contingency for as many scenarios as possible, not the least of which is power. Many legacy firewalls only offer a single power supply. Newer models offer a second power supply to ensure business continuity if one power supply fails.
Why upgrade: While the current NSa line and last-generation NSA series both include a single power supply, the NSa 2650-9650 have an additional slot to add an optional second power supply for critical redundancy.
About SonicWall NSa Next-Generation Firewalls
The SonicWall Network Security appliance (NSa) Mid-Range Firewall series consolidates automated advanced threat prevention technologies in a mid-range next-generation firewall platform. To go in-depth on the NSa range of firewalls, explore the specifications table below or download the complete SonicWall NSa data sheet.
What is SSL VPN?
There are a lot, and we mean a lot of acronyms in the world of IT.
Two of which include SSL VPN.
Starting at the very beginning, we look at breaking these down and demonstrating how they affect businesses and individuals and why choosing the right route is essential.

Definition of SSL VPN
SSL VPN - Secure Sockets Layer. Virtual Private Network. A protocol used in everyday web browsers that provide remote access securely through a VPN connection.
Using secure encryption end to end, the job of an SSL-VPN is to ultimately protect data that is sent, received and obtained between the device client’s software and the VPN client-server.
Benefits of SonicWall VPN for modern-day working
More businesses are now taking advantage of using SSL VPN clients as they look to increase the number of workers remotely requiring access to their network and resources. Creating a secure internet passage for all who are working online from outside of the company’s four walls.
The biggest benefit of SonicWall VPN is that it is easily installed and doesn’t require any specialised client software.
It also provides a more reliable connection for your remote workers providing higher compatibility with configurations and platforms of firewalls and networks.
Using an SSL VPN client means you can encrypt all network traffic, allowing remote workers access to restricted networks and resources securely, all through an authenticated pathway.
This level of security also prevents unwanted cyber visitors from obtaining sensitive information or eavesdropping on any private and confidential communications.
SSL VPN offers flexible and secure options for anyone working remotely who requires access to private business networks.
But how do they achieve all of this?
By allowing approved users a secure connection through standard web browsers to internal HTTP and HTTPS services, all enabling direct access to the client’s applications, resources and networks.
SSL VPN Types
VPN Portal – enables access to remote websites through one connection at a time. Authenticated remote users gain access to SSL VPN through their browser through an approved method/gateway, where access is achieved via a dedicated web page that acts as a portal for other services.
VPN Tunnel – is where access to multiple services can all be achieved securely via all standard browsers, non-web-based applications and other protocols. The tunnel should be thought of as a circuit established between a remote user and VPN server, where the server can connect to one or more remote websites, services, resources at any time. The SSL tunnel handles live content and offers a function that is not obtainable via other means.
A further advantage of SSL-VPN is that using TLS technology implemented in modern web browsers, which means you don’t need to install any specific software. Hence, it is easy to deploy.
There’s also less of a requirement for IT personnel to provide technical support, due to the ease of use of the client.
And unlike other security protocols you don’t need to download any additional software or configuration files, with no complex steps to follow, SonicWall's VPN simply needs an updated browser to establish a secure network.
As a business, you can also restrict remote users to particular applications instead of allowing your whole network to be accessed, keeping you in complete control at all times.
Important points to note
Remote workers' devices should be updated with anti-virus software to avoid malware spreading.
Training sessions for remote workers also help with keeping standards high and act as a good reminder that sessions should be closed down properly and not left open for all who have access to that device, view, for example.
We’d also advise not to use a public computer to set up an SSL VPN connection. In these instances, you can open yourself and your systems up to more cyber-attacks, offering up your confidential information and more to those that you don’t want to give it to.
SonicWall's VPN provides secure remote access to the network using the NetExtender client. Downloaded transparently, you can run any application securely on your computer network.
Ultimately, this is a seamless solution that allows secure access to your resources on your local network.
To find out more about SonicWall VPN and firewall solutions, give us a call on 0333 2405667.
Read the next blog: A Virtual Firewall that Protects Multi-Cloud Environments


















